In today’s cybercrime-ridden world, it’s important to understand the different types of network security protection available.
By understanding the strengths and weaknesses of each option, you can make an informed decision about which security solution is right for your business.
In this blog post, we’ll outline the different types of network security protection, including firewalls, access controls, email security, antivirus software, network segmentation, and more.
We’ll also provide some helpful tips for choosing the right solution for your business.
Understanding the Different Network Security Types
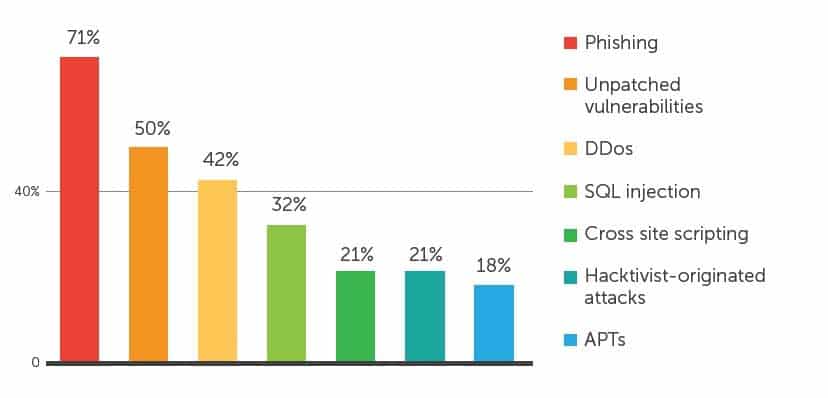
Data breaches and cyberattacks have become all too common, and without proper network protection, companies are at risk for potentially disastrous consequences.
60% of small businesses that suffer a cyber attack go out of business within a year, according to the US National Cyber Security Alliance.
The different types of network security reduce the risk of system misuse or theft of sensitive data, guard against unauthorized access, and ensure reliable authentication procedures are in place so only authorized personnel can gain access to the system.
With comprehensive solutions like firewalls, malware scanning and up-to-date patches deployed throughout your network stack, these network security types keep your systems running securely.
Read on to learn more about:
- Different types of network security
- Different types of encryption in network security
- Different types of scanning in network security
Different Types of Network Security
1. Firewall
Firewalls act like a perimeter barrier, providing an extra layer of protection against malicious actors attempting to access your network or files. Firewalls generally work by filtering data based on the content, the source from which it’s coming, or its destination.
Typically, they use established rules that specify what type of traffic can pass through and which will be rejected, as well as logging information about different connections for future reference.
2. Network segmentation
Boundaries are defined between segments of a network whose assets are related in function, risk, or role through network segmentation.
Segmenting the network reduces the attack surface, improves access control for network and data, and can even improve network performance. According to statistics, 96% of organizations now segment their networks.
3. Access Controls
Access controls allow your organization to decide who can and cannot access data, applications, and other resources on their network.
They also help to track activity and network traffic. By having these network security tools in place, your business can ensure that only authorized personnel with valid credentials have access to network assets and can reduce the risk of cyber threats.
A Data Breach Can Cost SMBs Up To $2.85 Million
Be Prepared With Network Security
Book Your Free Consultation4. Email Security
Email security is an essential component of cybersecurity, as these protocols protect your emails from external threats such as viruses, phishing attempts, denial-of-service (DoS), and cyber-attacks.
Some examples of email security protocols include TLS (Transport Layer Security) and S/MIME (Secure/Multipurpose Internet Mail Extensions).
TLS is used to encrypt and authenticate messages; this prevents hackers from intercepting or reading your emails.
S/MIME further strengthens email encryption by allowing digital signatures to be included in a message. This ensures that the message is sent by the true sender, protecting it from impersonation attempts.
5. Data Loss Prevention (DLP)
Data Loss Prevention (DLP) is a comprehensive approach to safeguarding confidential or sensitive data.
It typically involves implementing policies, technologies and processes for protecting data stored on computers, in databases, and on all types of devices that might leave the premises.
DLP also includes monitoring user activity to ensure all data is accessed, used, processed and stored in accordance with your company policy.
Aside from these network security types, there are many other forms of wireless security a managed service provider (MSP) can help you implement within your business, including virtual private networks, behavioral analytics, and more.
Check out these additional resources to learn more about the importance of cybersecurity and how a trusted MSP like InfoTECH can help.
Different Types of Encryption in Network Security
In exploring the different types of encryption in network security, there are several types of encryption used by businesses, including:
- Symmetric key encryption which is used when two or more entities have a shared secret key
- Asymmetric key encryption where public and private keys are used independently by different entities to encode messages; message authentication codes (MACs) which are used to authenticate received messages
- Digital signatures which provide authentication and integrity of sent messages
- Hash functions which produce a fixed length output string representing the data
While these methods differ in application, they all guarantee robustness and safety of data communications over your networks.
Different Types of Scanning in Network Security
There are many different types of scanning in network security that all play a vital role in safeguarding your web security and application security.
The most common types of network security scanning are:
- Vulnerability scanning
- Port scanning
- OS detection
Vulnerability scans look for any known weaknesses associated with the hardware and software that make up the system.
Port scanning checks the open ports available on your devices to detect potential threats.
Finally, OS detection scans search for different operating systems in an effort to detect any malicious activity taking place within the network.
For maximum protection against cyberattacks, these types of scans should be conducted regularly and continuously monitored.
How InfoTECH Can Help
As evident, there are many types of network security being used today to take necessary precautions against cyber crime.
If you’re looking for a trusted partner to help safeguard your computer systems and wireless networks, look no further than InfoTECH.
With over 17+ years helping businesses implement network security measures, you can trust us to keep your network secure.
Book a free consultation to learn more about your options!


