Have you ever looked at the smart devices in your office or home and wondered if they’re silently paving a direct path for cybercriminals? Kaspersky blocked over 1.51 billion IoT breaches in the first half of 2021.
As time goes on, cyber threats have evolved, and our connected devices have become increasingly sophisticated yet also more vulnerable. Every connected sensor, camera, or thermostat can become a new hacking gateway.
60% of small companies that get hit by a cyber attack go out of business within six months. This startling statistic underscores how rapidly a single breach can upend an entire enterprise.
“The future of IoT security hinges on proactive measures—those who wait reactively will always be one step behind,” says Brian Leger, Co-founder of InfoTECH Solutions.
Keep reading to discover the eight most urgent security landmines lurking in your connected environment and learn exactly what you can do about them.
The 8 Biggest IoT Cybersecurity Landmines You Must Avoid
It’s tempting to embrace every gadget that promises convenience, but the hidden threats are just as impressive. Below are eight cybersecurity landmines you’ll want to see and sidestep before it’s too late.
1. The Visibility Voids
Before you can protect your IoT environment, you need to see it clearly. A massive stumbling block in IoT and cybersecurity is the simple fact that many organizations have zero visibility over all the devices on their networks. From smart TVs in conference rooms to biometric scanners at entry points, each device represents a hidden layer of potential vulnerabilities.
What’s the Risk?
When you don’t know what devices exist, you can’t patch them or monitor their behavior. Unidentified endpoints open the door to rogue device connections, making it child’s play for attackers to penetrate your network.
Actionable Tip:
Map every single IoT device connected to your infrastructure—yes, even that smart coffee machine in the breakroom. Network segmentation also goes a long way: isolate IoT devices from your core business data to minimize lateral movements in case of a breach. Finally, implement a real-time monitoring tool that flags suspicious device activity.
2. Vulnerable Defaults
Many manufacturers ship devices with default usernames and passwords, like “admin” or “12345.” This might feel convenient, but it’s one of the most glaring IoT challenges you face every day.
What’s the Risk?
Attackers can exploit these well-known defaults, brute-forcing or guessing login credentials in seconds. Once they’re in, they can move around your system, tamper with devices, or steal data without detection.
Actionable Tip:
Change these default credentials immediately upon installation. Implement multi-factor authentication, especially for critical devices. Make a routine habit of password audits—outdated or weak passwords are your worst enemy.
3. Data Exposure
When was the last time you questioned how data—especially sensitive information—travels between your IoT devices and storage systems? One of the biggest issues in cybersecurity for IoT is weak or nonexistent encryption for data in transit or at rest.
What’s the Risk?
If devices transmit or store data unencrypted, an attacker can easily intercept it, leading to a data breach that damages your finances and your reputation.
Actionable Tip:
Adopt end-to-end encryption protocols. This means data remains encrypted from the moment it leaves your device until it arrives at its final destination. Combine that with robust key management and secure APIs to eliminate gaps where attackers can slip in.
Fortify Your IoT Network with Trusted Cybersecurity Experts
Over 20 Years of Experience, One Secure Solution.
Contact Us4. Legacy Systems
Not every device you deploy is brand-new. Legacy systems, which might be a year or even a decade old, create dangerous cracks in cyber security and infrastructures related to the Internet of Things.
What’s the Risk?
Older devices typically lack the advanced security features found in newer models. Their operating systems may no longer receive official updates, exposing them to well-known vulnerabilities that hackers love to exploit.
Actionable Tip:
If possible, decommission or upgrade legacy devices. When that isn’t feasible, apply virtual patches through network solutions that identify and block exploit attempts. Remember: security patches often don’t exist for devices that are no longer supported by manufacturers, so isolating these devices from critical systems becomes vital.
5. Poor Update Hygiene: The Achilles’ Heel of Internet of Things Cybersecurity
There’s one monumental oversight that torpedoes Internet of Things cybersecurity across countless organizations: a lax attitude about firmware and software updates. Each neglected update is a glowing neon sign advertising known vulnerabilities to hackers.
What’s the Risk?
Cybercriminals actively scan for out-of-date devices. Once they spot an unpatched vulnerability, they’ll infiltrate your system to steal data or disrupt operations.
Actionable Tip:
Schedule and automate firmware updates. Put someone in charge of checking all devices—preferably weekly—to ensure the latest updates are applied. This small step keeps you several strides ahead of opportunistic attackers.
6. Overlooked Supply Chain Gaps
It’s easy to trust the brand name on your device, but what about each component inside it—or the software libraries supporting it? Many organizations overlook supply chain vulnerabilities, giving hackers a backdoor right into your setup.
What’s the Risk?
If a single supplier is compromised, malicious code or hardware can reach you without ever sounding an alarm. From counterfeit components to malware-laden firmware, the risk is very real.
Actionable Tip:
Vet your suppliers thoroughly. Ask for certifications, vulnerability assessments, and compliance reports. It’s also wise to standardize security processes across your supply chain, requiring all vendors to meet strict cybersecurity criteria.
7. Security vs. Usability
Do you allow full device functionality for maximum user convenience, or do you lock everything down to bulletproof your defense? Balancing these two can feel impossible.
What’s the Risk?
If security measures are too strict, you risk employees finding shortcuts—like writing down passwords or disabling features. If you ease up too much, your defenses develop holes big enough for attackers to stroll through.
Actionable Tip:
Seek user-friendly solutions like single sign-on (SSO) and straightforward multi-factor authentication. Provide training that explains why certain security measures are non-negotiable. When employees understand the “why,” they’ll be more likely to comply.
| Interested in learning more about cybersecurity? Check out these blogs: The Complete Cyber Insurance Checklist 7 Most Common IT Problems for Businesses Why Network Security is Important for Your Business |
8. Insider Threats: The Dangers Within
Not every threat originates from the outside. Whether it’s deliberate sabotage or accidental misuse, insider threats loom large in IoT setups.
What’s the Risk?
From naive employees clicking phishing links to disgruntled staff stealing data, insider threats can unleash significant damage quickly—often without raising alarms until it’s too late.
Actionable Tip:
Conduct thorough background checks, enforce role-based access control, and run periodic security awareness training. A well-informed team is your best line of defense, because they understand how a careless slip can escalate into a costly crisis.
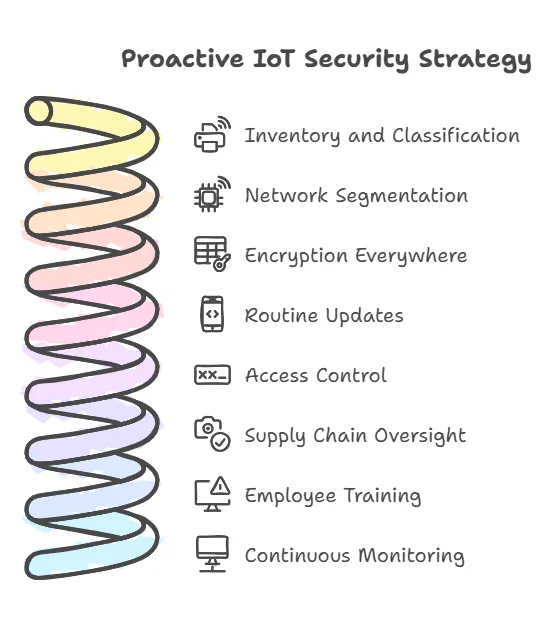
Your Step-by-Step Defense: Actionable Strategies for Proactive IoT Cybersecurity
Securing your IoT environment requires more than isolated tweaks. You need a coordinated strategy:
- Inventory and Classification: Start by listing all IoT devices, categorizing them by risk level.
- Network Segmentation: Separate IoT traffic from sensitive corporate data.
- Encryption Everywhere: Implement encryption for data at rest and in transit.
- Routine Updates: Automate firmware and software patches.
- Access Control: Use MFA, remove default credentials, and enforce strict password policies.
- Supply Chain Oversight: Adopt standardized security checks and demand transparency from your vendors.
- Employee Training: Equip your team with the knowledge to identify and report threats.
- Continuous Monitoring: Deploy real-time threat detection systems to spot anomalies before they cause havoc.
Quick-Fix Guide to IoT Challenges
| Challenge | Key Threat | Recommended Fix |
| Visibility Void | Blind spots, rogue devices | Comprehensive inventory, network segmentation |
| Vulnerable Defaults | Default credentials easily compromised | Change defaults, enable MFA, regular password audit |
| Data Exposure | Unencrypted data vulnerable to interception | End-to-end encryption, secure APIs, key management |
| Legacy Systems | Outdated devices lack modern security features | Decommission or isolate legacy devices |
| Poor Update Hygiene | Known vulnerabilities exploited by hackers | Automated firmware updates, zero-tolerance policy |
| Overlooked Supply Chain Gaps | Malicious components from third-party vendors | Vet suppliers, demand compliance and transparency |
| Security vs. Usability | Weak security from user workarounds if too complex | User-friendly MFA, continuous training |
| Insider Threats | Employees exploiting or mishandling privileged access | Role-based permissions, security awareness training |
Elevate Your IoT Cybersecurity—Contact InfoTECH Solutions Today
IoT devices enhance efficiency, but each connected endpoint also brings fresh security hurdles. From overlooked updates to easy-to-guess credentials, the vulnerabilities stack up quickly. By addressing everything from visibility blind spots to insider threats, you fortify your network against opportunistic hackers.
| Get Future-Proofed IT Solutions Near You | |||
| Lafayette | New Orleans | Baton Rouge | Lake Charles |
InfoTECH Solutions stands ready to guide you with robust cybersecurity planning, cutting-edge threat detection, and proven best practices to protect your IoT ecosystem. Ready to strengthen your defenses? Contact InfoTECH Solutions for more details and to schedule a comprehensive consultation. Act now to safeguard the powerful benefits that IoT can bring—without risking your peace of mind.



