Every business faces the daunting challenge of protecting its digital assets from an ever-growing array of cyber threats, especially when cybercrime is growing rapidly. Research shows that there were 2,365 cyberattacks in 2023, with 343,338,964 victims.
Without a comprehensive cyber security assessment checklist, your organization is vulnerable to data breaches, financial losses, and reputational damage.
As Brian Leger, Co-Founder of InfoTECH Solutions, says, “Identifying and mitigating security risks is not just an IT concern; it is a critical business function that requires a strategic approach.”
The stakes are high, and the consequences of inaction are severe. This blog provides a checklist to guide you through evaluating your current security measures and implementing improvements to protect your business from potential cyber threats.
Complacency in Cybersecurity: Why Your Defenses Need an Upgrade
Many businesses mistakenly believe that their current security measures are sufficient to protect against cyber attacks. However, with the rapid evolution of cyber threats, relying on outdated security practices can leave your organization vulnerable. Companies must regularly assess their security posture to identify gaps and strengthen their defenses.
Are Your Cyber Security Measures Enough to Stop an Attack?
Stay ahead with InfoTECH Solutions' proactive security measures.
Learn More1. Identify and Classify Assets
Begin your cyber security assessment by identifying all your organization’s assets, including hardware, software, and data. Classifying these assets based on their sensitivity and importance is crucial. Understanding which assets are most critical to your operations will help you prioritize your security efforts.
- Inventory all hardware and software assets.
- Classify data according to its sensitivity (e.g., public, internal, confidential).
- Identify critical business processes and their dependencies.
2. Evaluate Current Security Measures
Assess your current security measures to determine their effectiveness. This evaluation should include both technical controls (e.g., firewalls and antivirus software) and administrative controls (e.g., security policies and employee training).
- Review existing security policies and procedures.
- Assess the effectiveness of firewalls, antivirus software, and intrusion detection systems.
- Evaluate the adequacy of physical security controls.
3. Conduct a Vulnerability Assessment
A thorough vulnerability assessment will help identify weaknesses in your information systems that could be exploited by cyber attackers. Use automated tools and manual techniques to discover network, application, and system vulnerabilities.
- Perform network scans to identify open ports and services.
- Conduct vulnerability scans on all systems and applications.
- Manually test for common security flaws (e.g., SQL injection, cross-site scripting).
4. Perform a Risk Assessment
After identifying vulnerabilities, assess the risks associated with each one. A risk assessment will help you understand the potential impact of a security breach and prioritize remediation efforts.
- Evaluate the likelihood and potential impact of each identified vulnerability.
- Categorize risks based on severity (e.g., high, medium, low).
- Develop a risk assessment process to evaluate new threats regularly.
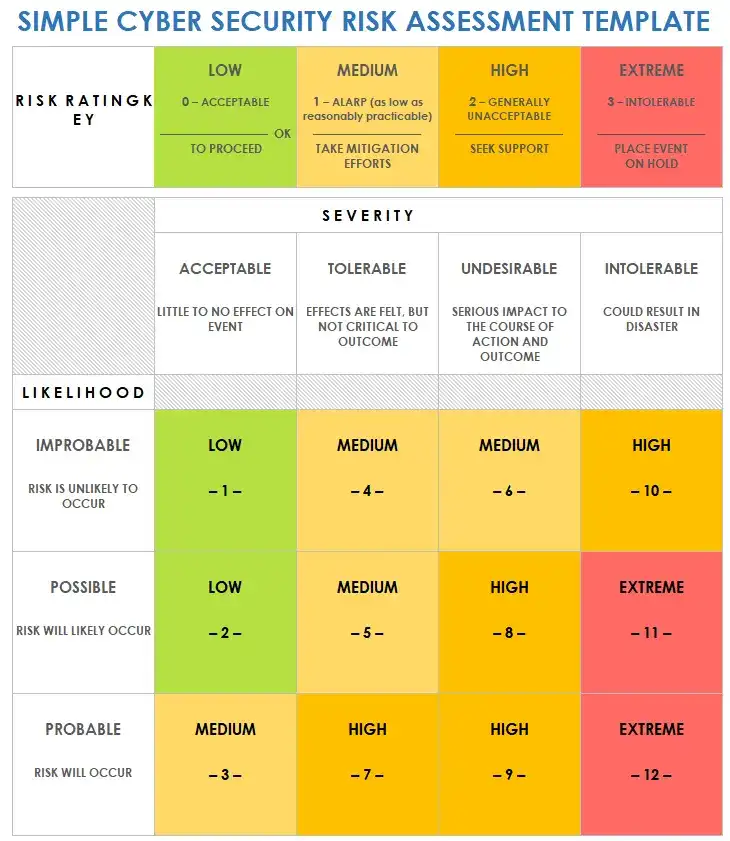
Source: Smartsheet
5. Develop a Threat Assessment Checklist
Creating a threat assessment checklist will help you systematically evaluate potential cyber threats. This checklist should include internal and external threats, such as malicious insiders, cybercriminals, and nation-state actors.
- Identify potential internal threats (e.g., disgruntled employees, human error).
- Assess external threats (e.g., cybercriminals, hacktivists).
- Evaluate the impact of natural disasters and other physical threats on your information systems.
6. Implement Access Controls
Did you know that research shows that 17% of all organizational sensitive files are accessible to all employees? Effective access controls are essential for protecting sensitive data and preventing unauthorized access. Strong authentication and authorization mechanisms can significantly reduce the risk of security breaches.
- Enforce strong password policies and multi-factor authentication.
- Implement role-based access controls (RBAC) to limit access to sensitive information.
- Regularly review and update access permissions.
7. Develop a Security Incident Response Plan
A well-defined security incident response plan will help your organization quickly and effectively respond to security breaches. This plan should outline the steps to take during an incident, including containment, eradication, and recovery.
- Create a detailed incident response plan with clear roles and responsibilities.
- Develop procedures for detecting and reporting security incidents.
- Conduct regular incident response drills to ensure preparedness.
8. Monitor and Review Security Measures
Continuous monitoring and regular reviews are essential for maintaining a strong security posture. Implementing automated monitoring tools and conducting periodic security assessments will help you identify and address new vulnerabilities and threats.
- Deploy security information and event management (SIEM) solutions for real-time monitoring.
- Conduct regular security audits and penetration tests.
- Review and update security policies and procedures annually.
9. Educate and Train Employees
Human error is a leading cause of security incidents. Without the right cybersecurity awareness training, your staff could unknowingly make your business vulnerable to attacks, says CloudSecureTech. Providing comprehensive security awareness training for employees is crucial and can help prevent common mistakes that lead to data breaches.
- Develop a security awareness training program.
- Conduct regular training sessions on topics such as phishing, social engineering, and safe browsing practices.
- Evaluate the effectiveness of training through tests and simulations.
10. Ensure Compliance with Regulatory Requirements
Compliance with regulatory requirements is crucial for avoiding legal penalties and maintaining customer trust. Ensure your organization adheres to relevant data protection laws and industry standards.
- Identify applicable regulations (e.g., GDPR, HIPAA, PCI-DSS).
- Conduct regular compliance audits.
- Implement necessary controls and documentation to demonstrate compliance.
Benefits of a Comprehensive Cybersecurity Assessment
| Benefit | Description |
| Identify Vulnerabilities | Helps uncover weaknesses in your systems and processes that could be exploited by cyber attackers. |
| Prioritize Risks | Enables you to focus on the most critical threats to your organization, optimizing resource allocation. |
| Enhance Security Measures | Provides insights into improving existing security controls and implementing new ones for better protection. |
| Ensure Compliance | Assists in meeting regulatory requirements and avoiding legal penalties. |
| Reduce Downtime | Helps develop effective incident response plans, minimizing disruption in case of a security breach. |
| Protect Sensitive Data | Safeguards critical information from unauthorized access and potential data breaches. |
| Boost Customer Trust | Demonstrates a commitment to security, which can enhance your reputation and build customer confidence. |
| Educate Employees | Raises awareness among staff about cybersecurity best practices and their role in maintaining security. |
Check Every Box in Your Cybersecurity Checklist with InfoTECH Solutions
A comprehensive Cyber Security Assessment Checklist is vital for identifying vulnerabilities, prioritizing risks, and implementing effective security measures. Regularly assessing your security posture will help you stay ahead of cyber threats and protect your organization from data breaches and other security incidents.
| Discover Trusted Cybersecurity Services in New Orleans, LA |
InfoTECH Solutions offers expert cybersecurity services to help businesses protect their sensitive data and information systems.
Our team of professionals can assist you in conducting thorough security assessments, developing robust security strategies, and ensuring compliance with regulatory requirements. Contact us today to schedule a free consultation and safeguard your business from cyber threats.



