It’s 2024, and the cloud is no longer an emerging technology but the backbone of many businesses. Yet, as its adoption has skyrocketed, so too have the security threats that target this vital infrastructure.
Research proves that security is a top concern for 81% of businesses that are considering moving to cloud technology.
These threats are not just technical issues; they represent significant business risks, from operational disruption to severe financial and reputational damage.
As Brian Leger, Co-Founder of InfoTECH Solutions, says, “Prioritizing cloud security is the hallmark of foresighted businesses aiming for sustainable success.”
This blog explores the top cloud security threats facing businesses today, offering insights into the evolving landscape of cyber risks and providing a roadmap for businesses to navigate these turbulent waters with confidence.
Understanding Cloud Security Threats
Cloud security threats are multifaceted and can come from various sources, whether external attackers, internal threats, or even from the cloud services themselves.
Moreover, cloud infrastructure, inherently complex and dynamic, can be challenging to secure without a comprehensive strategy. Acknowledging the complexity and variety of these threats is the first step toward robust defense.
1. Data Loss
The cloud offers unparalleled flexibility and scalability, but it also introduces a unique set of security threats in cloud computing.
One primary concern is data loss. Insights from Statista confirm that 64% of respondents said data loss and data privacy are the leading cloud security concerns. Whether through malicious attacks or accidental deletions, the loss of critical data can cripple a business.
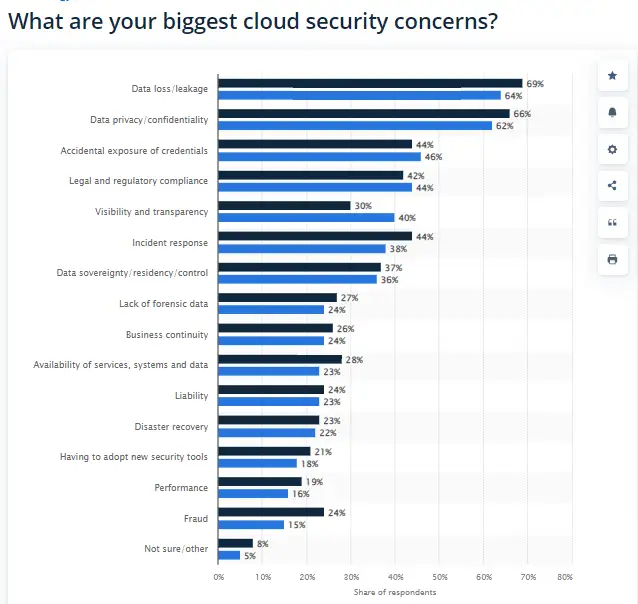
Source: Statista
2. Data Breaches
Data breaches remain a top concern in cloud environments. These breaches can result from various vulnerabilities, from flawed system configurations to sophisticated cyber-attacks, underscoring the need for comprehensive security strategies.
These incidents not only lead to significant financial losses but also damage an organization’s reputation. In 2023, the average cost of a breach in a hybrid cloud environment was a whopping $3.61 million.
3. Insider Threats
Unlike external threats, insider threats come from within the organization— Whether intentional or accidental, from disgruntled employees, negligent staff, or even insiders who fall prey to phishing schemes.
These individuals already have access to the cloud infrastructure, making their actions particularly damaging. Addressing insider threats requires a combination of access control, user behavior monitoring, and cybersecurity training.
Cloud Security Concerns Keeping You Up at Night?
InfoTECH Solutions delivers top-tier security measures to protect your digital assets.
Learn More4. Account Hijacking
Account hijacking is a type of attack where threat actors gain control of users’ accounts, often through phishing or exploiting security vulnerabilities. Once inside, they can access sensitive data, disrupt operations, and even use the compromised account to launch further attacks.
5. Public Cloud
The public cloud’s scalability and accessibility are double-edged swords. While they provide significant benefits, they also expand the attack surface, offering more opportunities for cybercriminals to exploit. Security teams must therefore be extra diligent in monitoring and securing these environments.
6. Insecure Interfaces and APIs
Cloud services often rely on APIs and interfaces that, if not properly secured, can become entry points for attackers. Ensuring the security of these components is critical to safeguarding cloud environments.
7. Advanced Persistent Threats (APTs)
APTs are sophisticated attacks where intruders gain access to a network and remain undetected for long periods. Protecting against APTs demands advanced detection and response strategies to identify and neutralize threats before they cause extensive damage.
Strategies for Mitigating Cloud Security Threats
1. Comprehensive Risk Assessment
Understanding the specific threats to an organization’s cloud environment is the first step in developing an effective security strategy. This involves a thorough risk assessment to identify vulnerabilities and prioritize threats.
Such assessments should be ongoing, adapting to new threats as they emerge and evolving with the organization’s cloud usage.
2. Enhanced Data Encryption
Encrypting data at rest and in transit provides a critical layer of protection, ensuring that even if data is intercepted or accessed, it remains unintelligible and useless to unauthorized individuals.
Moreover, robust encryption strategies must complement strong key management practices to enhance security.
3. Robust Access Control Measures
Implementing strong access control measures, including multi-factor authentication and least privilege access, can significantly reduce the risk of insider threats and unauthorized access.
These controls should be dynamic, adapting to an organization’s changing roles and requirements to prevent excessive access rights.
4. Continuous Monitoring and Threat Detection
Real-time monitoring of cloud environments helps detect unusual activities or breaches early, enabling rapid response to mitigate potential damage.
This proactive approach should be integrated with comprehensive analytics to discern patterns and predict potential security incidents before they occur.
More resources you might like:
5. Employee Training and Awareness
Human error remains a significant vulnerability in cloud security.
Regular training and awareness programs can equip employees with the knowledge to recognize and prevent security breaches. These programs should be continuous, reflecting the evolving nature of cloud threats and reinforcing the importance of security in everyday operations.
6. Incident Response Planning
An effective incident response plan ensures that an organization can quickly and effectively respond to security incidents, minimizing damage and restoring operations as swiftly as possible. This plan should be regularly tested and updated to ensure it remains effective against the backdrop of an evolving threat landscape and changing organizational structures.
Comparative Analysis of Cloud Security Measures
| Security Measure | Implementation Ease | Cost-Efficiency | Impact Level | Best Suited for |
| Endpoint Security | Moderate | High | High | Organizations with numerous remote users |
| Network Traffic Analysis | Challenging | Moderate | High | Enterprises with significant data flow |
| Security Policy Enforcement | Moderate | High | Medium | All cloud-dependent organizations |
| Public and Private Key Encryption | Complex | Moderate | High | Businesses with sensitive data |
| Regular Security Training | Easy | Low | Medium | All organizations |
| Disaster Recovery Planning | Moderate | Moderate | High | Businesses requiring high availability |
| Two-Factor Authentication | Easy | Low | High | Organizations with external user access |
| Cloud Service Provider Audits | Moderate | Varies | High | Enterprises using multiple cloud services |
| Data Redundancy Solutions | Moderate | High | Medium | Organizations with critical data |
| Application Security Testing | Challenging | High | High | Organizations with custom cloud applications |
Build a Resilient Cloud Infrastructure with InfoTECH Solutions
In the ever-evolving landscape of cloud computing, staying ahead of security threats is crucial for maintaining the integrity and trustworthiness of your business operations.
The strategies outlined here provide a comprehensive approach to mitigating risks, emphasizing the necessity of proactive measures and organizational agility in tackling cloud security challenges. We recognize that navigating these complexities can be daunting, but you’re not alone in this journey.
Looking for Reliable Managed IT Services in Your Area? We Can Help:
InfoTECH Solution stands at the forefront of cloud services, offering expert guidance and robust solutions to navigate the complex landscape of cloud security.
Don’t let your organization be caught off guard. Contact InfoTECH Solutions today to schedule a free consultation and fortify your cloud defenses against tomorrow’s threats.



