Zero trust network segmentation (ZTNS) is a security strategy that divides a network into smaller, isolated segments to control and limit the data flow between them. This strategy ensures that if an attacker accesses one part of your network, strict boundaries prevent them from moving to other parts of your network.
| “Your security controls need careful thought. It’s too easy to prioritize convenience and accessibility in areas where that shouldn’t be your main concern.” – Brian Leger, Co-Founder of InfoTECH Solutions. |
Not every organization needs to use zero trust segmentation, but it is strongly recommended in most cases. Also, some compliance frameworks may enforce a zero trust architecture to meet regulations. Check with your compliance standards to verify if this is a requirement for you.
However, since it is still strongly recommended for most organizations, this article will explore the benefits and the steps that you can take to adopt a zero trust security framework.
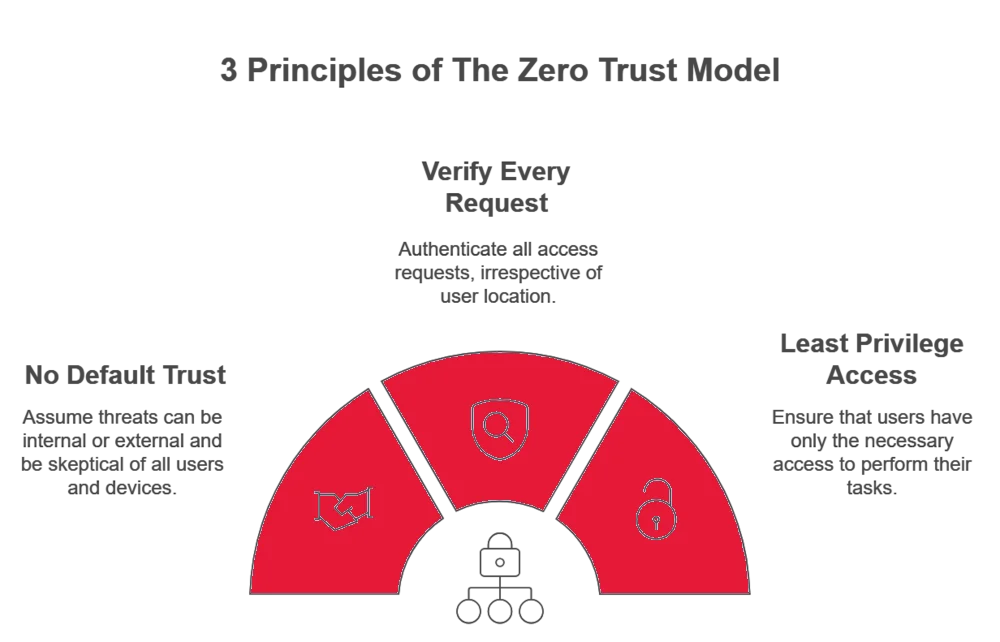
What Are The 3 Principles of Zero Trust Network Security?
The 3 principles of zero trust segmentation encourage organizations to protect their networks by thoroughly verifying each access request and never taking anyone’s security for granted. This approach strengthens security by making sure your employees can only access essential resources.
These 3 principles are demonstrated below.
5 Key Reasons to Implement Zero Trust Network Segmentation
1. Limit Threat Spread
Zero trust network segmentation restricts access to specific parts of a network. This strategy contains potential attacks by preventing lateral movement between segments. As a result, sensitive data and applications are safer, and the risk of widespread damage is lower.
2. Control Access & Improve Compliance
ZTNS enforces strict access policies that align with compliance standards and offer precise control over who can access which parts of the network and for what purpose. This system reduces your risk of unauthorized access and helps you meet regulatory requirements.
Reduce Your Risks With 24/7 Cybersecurity Services From an A+ BBB-Accredited Team
3. Reduced Attack Surface
By breaking down a network into isolated segments, ZTNS reduces the number of potential access points that attackers can exploit. With fewer access points available, attackers face more barriers, making it easier for IT teams to monitor and defend against potential threats.
4. Enhanced Visibility & Control
ZTNS gives IT teams a continuous view of network activity across all segments. This visibility helps them detect unusual behavior quickly, which allows for faster detection and response. CloudSecureTech points out that 97% of applications have at least one security vulnerability, and having this level of visibility will help you proactively spot any on your network.
5. Adapt to Modern Work Environments
A higher number of businesses are allowing remote work and leveraging cloud environments. ZTNS secures access to network resources regardless of the user’s location, making it ideal for both situations. This flexibility supports efficient network management across diverse work settings.
How to Implement Zero Trust Segmentation: Step-by-Step
1. Identify & Classify Assets
Begin by identifying all assets on the network, including devices, applications, and data. Classify these assets based on sensitivity and importance to prioritize protection efforts. This helps create a foundation for precise segmentation and granular access controls.
2. Map Data Flows & Communication Paths
Understand how data moves across your network by analyzing communication patterns between assets. Mapping data flows helps you determine ideal points for segment boundaries and create access controls that limit exposure.
3. Define Access Policies
Implement access policies that follow the “least privilege” model, where users and devices only receive the minimum access they need. By limiting access within each segment, you reduce the possibility of unauthorized users moving freely across your network.
4. Segment The Network
Divide your network into isolated sections based on the classification of assets and mapped data flows. Each segment should include strict entry and verification points to control access.
There are a few different types of network segmentation you can use depending on the asset. Here are some examples.
| Segmentation Type | Description | Best Use Case |
| Physical Segmentation | Uses separate physical hardware, like switches or routers, to create isolated segments. Ideal for high-security assets that require strong isolation. | Sensitive environments with physical security requirements |
| Virtual Segmentation | Divides networks using VLANs or VPNs, creating virtual boundaries within a single physical network. Useful for segmenting departments or groups within an organization. | Departmental separation or internal organization |
| Application Segmentation | Restricts access to specific applications or services, allowing only authorized users or systems. Often used to protect sensitive applications, such as financial or HR systems. | Securing access to critical applications |
| Micro-Segmentation | Breaks down segments further to isolate individual workloads or processes within applications, providing fine-grained access control. Common in environments with high compliance needs, like healthcare or finance. | High-compliance environments needing fine-grained access control |
5. Implement Continuous Monitoring
Use continuous monitoring to track unusual activity within segments and allow for real-time threat detection and response. Since a cyber attack occurs every 39 seconds, ongoing monitoring is essential to identify potential threats and maintain data flow control.
6. Test & Adjust Regularly
Regularly test your segmentation strategy to identify weaknesses and adjust access policies as needed. Frequent testing ensures that your ZTNS implementation remains effective as your network and technology standards evolve.
| Get Expert Advice From Expert IT Consultants in Louisiana | ||
| New Orleans | Lafayette | Baton Rouge |
Make The Most of Zero Trust Network Segmentation Using Advice From Experts
Although 93% of business leaders consider network segmentation critical to security, only 30% of organizations have actually implemented it. This surprising disconnect is largely due to a lack of understanding of how the zero trust model can fit into a specific network.
If you need help tailoring the zero trust model to your business, ask InfoTECH Solutions. We can guide you through a tailored implementation strategy and provide 24/7 network monitoring once you’re all set up.
Reach out today to get started.



