Managing permissions in SharePoint isn’t about ticking boxes. It’s a critical process that helps reduce risks, improve collaboration, and control IT costs. 70% of breached organizations attribute the incident to excessive third-party access.
| “Good governance is a pillar of sustainable IT strategy and critical to maintaining an impenetrable technology infrastructure” – Brian Leger, Co-Founder of InfoTECH Solutions |
Teams face rising compliance pressure and increasing costs. Clear permissions keep your SharePoint secure and help your teams focus on their work.
Here, we cover practical SharePoint permission best practices that protect your data, save time, and align IT with real business needs.
Why Follow SharePoint Permission Best Practices?
Following these best practices isn’t just a formality. It directly improves your security and supports your business goals.
- Lower risk of unauthorized access: Misconfigured permissions lead to accidental exposure. Giving the right permissions ensures sensitive files are visible only to those who need them.
- Cut unnecessary IT costs: Poorly managed permissions increase support tickets and manual fixes. Clear structures reduce daily issues, saving your IT team time and budget.
- Support compliance requirements: Regulations often require proof of controlled access. Documented permission policies help meet these standards and avoid penalties.
- Keep collaboration running smoothly: When permissions reflect real roles, teams access what they need without delays. This keeps projects moving without constant admin involvement.
Strengthen Your SharePoint Security with InfoTECH Expertise!
Work with a trusted MSP Verify™ certified partner to simplify permissions, reduce risk, and stay compliant.
Talk to UsTop 10 SharePoint Permission Best Practices That Work
Clear and well-structured permissions do more than protect data. They help teams avoid confusion, save time, and reduce support issues.
When you follow the proper steps, you make SharePoint easier to manage and safer to use. Let’s examine each practice in detail so you can apply it confidently.
Manage Permissions at the Site Level
Applying permissions directly to files and folders might seem quick, but it creates a system that’s hard to track and manage over time. Every new document or folder would need manual updates, and missing one could expose sensitive data.
Instead, set permissions at the site level. This creates a clear parent-child structure, where everything inside the site inherits the same rules automatically. New documents, libraries, or folders will get the correct access without extra work. This keeps your system organized, reduces mistakes, and saves time when you add new content.
When you manage permissions this way, it also becomes easier to review and update access across your team. You won’t need to check hundreds of files one after the other. One update at the site level is all it takes.
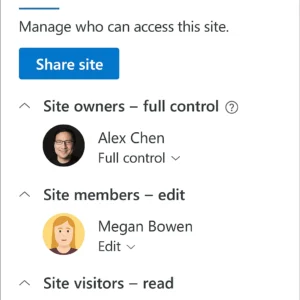
Use Built-in Security Groups
SharePoint provides three built-in groups: Owners, Members, and Visitors. Each group has a specific role:
- Owners have full control and can change settings and manage permissions.
- Members can add and edit content, which supports daily work.
- Visitors can view content but can’t make changes.
Using these groups keeps your permission structure clear and consistent. It prevents confusion because everyone knows the actions each group can execute. It also avoids situations where someone accidentally gets too much access.
Relying on built-in groups also helps new site admins understand the system quickly. They won’t have to guess what custom groups do, making training and onboarding simpler.
Control External Sharing Carefully
Sharing content with external partners and clients is useful for collaboration. However, it also brings extra risks if it isn’t controlled.
Start by turning off external sharing on sites that don’t need it. For sites that require external access, document exactly why it’s needed and who can approve new external users. This keeps your sharing decisions clear and accountable.
Regularly review which sites allow external sharing. Remove permissions that are no longer needed. A large part of data leaks happens because files are shared too broadly without proper review. Taking a careful, documented approach prevents this from happening.
Apply the Principle of Least Privilege
External actors cause 65% of breaches, while 35% stem from internal sources, primarily employee mistakes rather than deliberate actions.
POLP means giving users only the access they need to do their work, no more, no less. It reduces the chance of someone accidentally changing or deleting important content.
Start by listing each user’s role and tasks. Match them to the lowest possible permission level that still allows them to work effectively. For example, if someone only needs to view documents, assign them to the Visitors group instead of “Members”.
Review permissions every quarter. Roles can change when people move to new teams or take on new tasks. Update permissions to ensure your system stays secure and efficient.
Remove Old Access Promptly
When projects finish or staff move to new roles, they often keep access they no longer need. Over time, these forgotten permissions can become security risks.
Set a schedule to review and remove outdated permissions at least every three months. This keeps your environment clean and makes sure only current team members can view or edit content.
Removing old access isn’t complicated. Use SharePoint’s built-in reports to see who has what access. Removing unused permissions protects sensitive data and keeps your structure simple.
Break Inheritance Only When Required
SharePoint automatically applies site-level permissions to all folders and documents inside the site. Sometimes, you need different permissions for a specific folder or document. This is called breaking inheritance.
Use this carefully. Breaking inheritance too often creates a patchwork of unique permissions that are hard to review and manage. It can confuse admins and lead to mistakes.
Before breaking the inheritance, document why it’s necessary and who approved it. Review these exceptions regularly to ascertain that you still need them. When you keep them rare, you protect your system’s clarity, and you make management easier.
Use Groups Instead of Direct Permissions
Adding permissions directly to individual users seems quick, but creates hidden complexity. Over time, it becomes hard to remember why someone has access or to track changes.
Instead, add users to groups based on their team or role. Assign permissions to the group, not the person. This way, adding or removing a user only requires moving them in or out of the group.
Groups mirror your team structure. It makes updates faster and keeps permissions clear. It also makes audits simpler because it’s easier to explain why each group has certain permissions.
Decide Between Microsoft 365 Groups and AD Groups
Both Microsoft 365 Groups and Active Directory (AD) security groups can manage permissions in SharePoint. Microsoft 365 Groups supports modern collaboration tools like Teams and Planner, while AD groups can offer tighter control across your organization.
Select one based on your organization’s needs and stick to it. Mixing them too much can make your structure harder to manage. Document your choice so new administrators understand why the system is set up that way.
This decision affects how you manage permissions and how your teams use tools. Take the time to plan it with your IT and compliance teams.
Set Safer Default Sharing Links
By default, SharePoint often creates sharing links that work for “People in your organization.” This means that anyone in your company who gets the link can open the file, even if it wasn’t meant for them.
Change the default to “People you choose.” This makes links work only for specific people you name when sharing. If someone forwards the email, it won’t work for others.
This small change prevents accidental oversharing. Document the reason for using this setting so your policy stays clear to all users.
Train Users and Review Regularly
Even with the best technical settings, users still play a huge role in securing SharePoint. Many users don’t realize the risks of broad sharing or why permissions matter. Research shows that firms that prioritize regular security training see a 70% drop in incidents.
Offer short, focused training sessions to explain the basics: what each permission level means, how to share safely, and why it’s important. Use real examples to show how things could go wrong.
Regular reviews help you catch changes in your team’s structure or tasks. Schedule them every three to six months.
| Find Out How Else You Can Make Each Work Day Easier What is IT Augmentation & How Do You Know When You Need It? What is AI Business Automation? 7 IT Procurement Best Practices You Need to Follow |
Custom Permission Levels for Unique Needs
Built-in permission levels cover most scenarios, but sometimes unique needs require custom settings.
- Identify the real need: Analyze why a custom level is needed. Avoid adding permissions because someone merely asks. Only include what the role truly requires.
- Document your changes: Write down what the custom level does and why it exists. This keeps your team aligned and helps during audits.
- Review regularly: Business needs change over time. Check custom levels quarterly to ensure they’re still relevant and safe.
- Avoid overusing custom levels: Too many custom levels create confusion. Keep them limited to special cases where standard options don’t work.
Tools to Simplify SharePoint Permission Best Practices
Manual tracking works early on, but tools keep your system manageable as your organization grows.
- vCIO and TAM roles: Virtual CIOs and Technical Account Managers review permissions quarterly. They align IT decisions with your business goals and keep leadership informed.
- ShareGate Permission Matrix Report: This report gives a clear view of who has access to what, including external users. It highlights risky settings so your team can act quickly.
- Automation and reporting tools: Automate reminders to review permissions and remove inactive users. These tools keep your SharePoint secure without extra manual effort.
Steps to Get Started with SharePoint Permissions
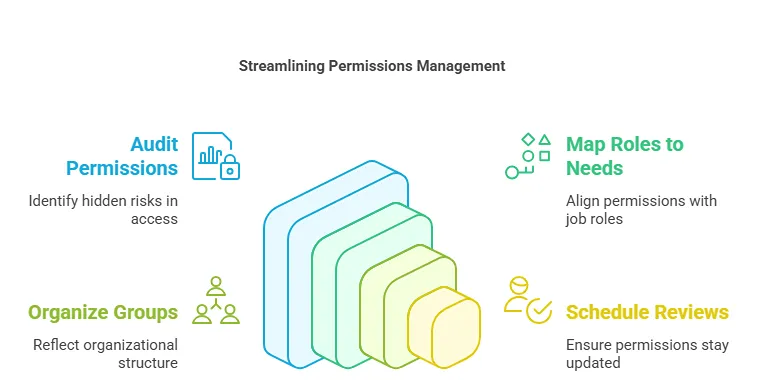
Improvements begin with clear, manageable steps.
- Audit your current permissions: Use built-in reports or tools like ShareGate to see your current access structure. This helps you spot hidden risks.
- Map roles to real needs: List each job role and match it to the required permissions. This keeps your permissions aligned with business functions.
- Use groups to match your organizational chart: Create groups that reflect the departments or teams within your organization. This enables the addition of new users quickly and ensures consistent permissions.
- Schedule quarterly reviews: Regular reviews catch outdated permissions before they become risks. Put them on your calendar so they don’t get missed.
Starting now with small steps builds a stronger, safer SharePoint environment.
Common SharePoint Permission Challenges and Solutions
Even with strong practices, teams run into challenges. Here’s how to solve them.
| Challenge | Solution |
| Too many custom permission levels | Limit to real needs; document each level’s purpose and review quarterly. |
| Old projects still have active users | Run quarterly audits and remove users who no longer need access. |
| Confusing inheritance breaks | Break inheritance only when necessary, and document every change. |
| Unclear sharing policies | Write a clear policy; include it in new user training sessions. |
| Direct permissions to users | Group users to simplify updates and reporting. |
Secure Your SharePoint Environment Today with InfoTECH Solutions
SharePoint permission best practices help protect your data, keep teams focused, and reduce IT overhead. With clear policies, smart use of groups, and regular audits, you can avoid access mistakes before they disrupt work.
InfoTECH Solutions helps businesses build and maintain these best practices. Backed by over 17 years in the industry and an MSP Verify™ certification, we support your team with proactive monitoring, security assessments, and guided processes to keep your SharePoint environment secure and manageable.
| Work With Some of Louisiana’s Leading IT Services Providers | ||
| New Orleans | Baton Rouge | Lafayette |
Get in touch with us to see how we can simplify and secure your SharePoint permissions strategy, strengthening it for the long term.



